An SPF record (Sender Policy Framework) is an email authentication system that mail servers use to make sure that emails that appear to come from your domain actually do come from you.
Basically, it’s designed to stop phishing attempts and scammers from sending fake messages that claim to be from legit domains.
Technically, you don’t have to set up an SPF record in order to send emails. But it adds a layer of security to your campaigns, which makes your domain more trustworthy to ISPs (internet service providers).
This makes it more likely that your emails stay out of spam.
That’s why it’s so important to set up an SPF record: to protect your domain from spoofing, and to keep your cold emails out of spam.
¶What does an SPF record do?
An SPF record simply identifies the mail servers that are allowed to send messages from your domain.
It’s a type of DNS TXT (Domain Name System ”text”) with a list of APIs, software, etc., that you’ve approved to send messages on your behalf.
It looks like this
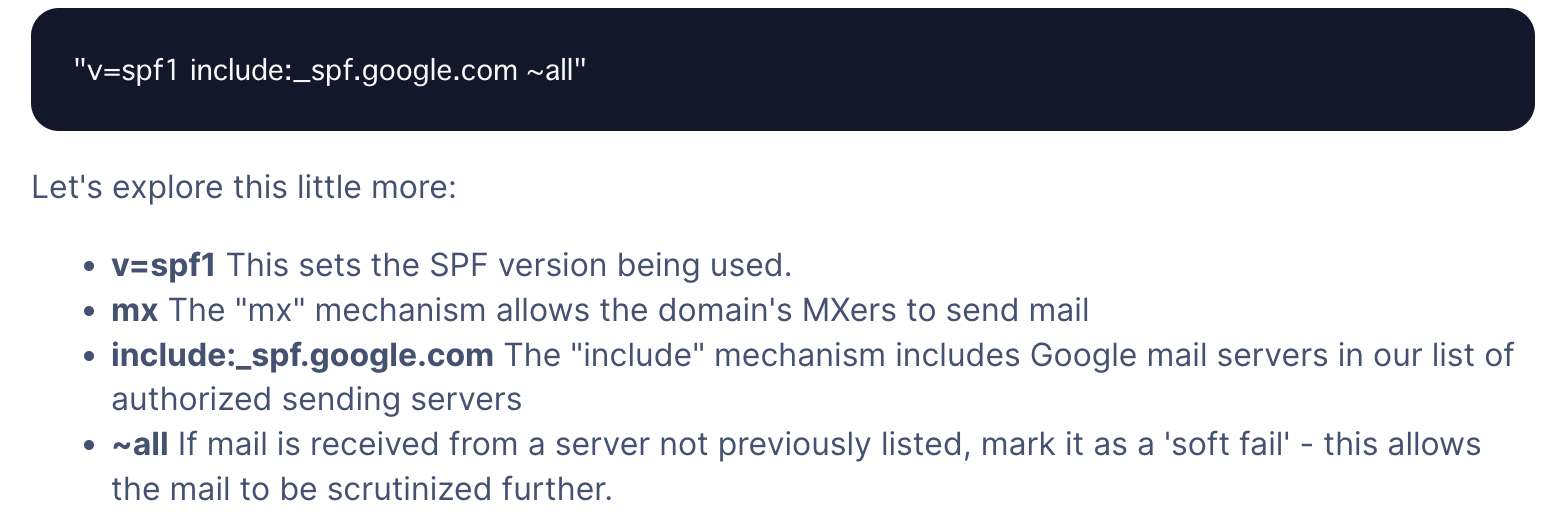
v=spf1 include:_spf.google.com ~all
- SPF-syntax
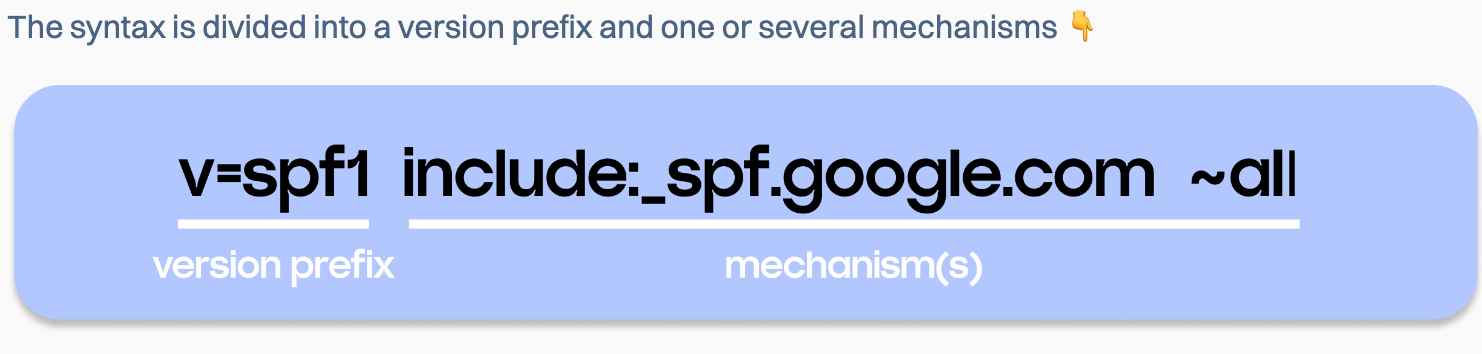
For example
v=spf1 ip4:40.113.200.201 ip6:2001:db8:85a3:8d3:1319:8a2e:370:7348 include:thirdpartydomain.com ~all
- Start with the SPF version v=spf1. This indicates that it is an SPF record. It will always be v=spf1, as other SPF versions have been discontinued.
- The SPF version tag should be followed with all IP addresses that are authorized to send email on behalf of your domain.
- for example: v=spf1 ip4:40.113.200.201 ip6:2001:db8:85a3:8d3:1319:8a2e:370:7348
- Next comes the “include” statement, which is needed for every third-party organization that sends email on your behalf.
- For example: v=spf1 ip4:40.113.200.201 ip6:2001:db8:85a3:8d3:1319:8a2e:370:7348 include:thirdpartydomain.com
- You should consult with these third parties to discover which domain to use as a value here. Also, ESPs typically publish SPF records for sending domains on your behalf, so you will want to verify with them as well.
- The end of the SPF record is the “all” tag. It is important because it indicates what policy and how strictly it should be applied when a receiving server detects a server which is not listed (authorized) in your SPF record.The “all” tag has the following basic options:
- -all – (fail) non-authorized emails will be rejected*
- ~all – (softfail) non-authorized emails will be accepted but marked*
- +all – this tag allows any server to send email from your domain, so we advise strongly against it.
*You can find more information about the differences between fail and softfail here.
For example: v=spf1 ip4:40.113.200.201 ip6:2001:db8:85a3:8d3:1319:8a2e:370:7348 include:thirdpartydomain.com ~all.
This is a basic overview of what an SPF record can contain. You can find a deeper look into SPF syntax here.
For your domains that do not send email (inactive or parked domains), it is recommended to publish an SPF policy that doesn’t include any IP addresses to prevent it from being abused. Here’s an example record for a non-sending domain:
v=spf1 -all
Note: SPF records cannot be over 255 characters long, and cannot include more than ten “include” statements, also known as “lookups.”
To inspect and verify your SPF records, head over to our free SPF Survey.